Welcome to our in-depth exploration of software reverse engineering! While we cannot possibly cover every aspect of this vast topic in a single article, we strive to provide you with a solid foundation and a thorough understanding of the core concepts. Focusing on the x86_64 architecture, this article will serve as a springboard into the fascinating world of reverse engineering. Be sure to keep an eye out for our follow-up articles as we delve deeper into this captivating subject.
In the ever-evolving world of software development, reverse engineering has become an invaluable tool for understanding and analyzing complex systems. This process, which involves disassembling software to reveal its underlying architecture and functionality, offers numerous advantages for programmers, security experts, and researchers alike. In this article, we will delve into the intricacies of reverse engineering, exploring its various applications and providing practical examples to illuminate its significance in software analysis.
Sit back, relax, and let’s embark on this journey together!
Meaning of Reverse Engineering
Reverse engineering is the art of deconstructing a software program or system to understand its design, architecture, and functionality. This process typically involves breaking down the compiled code into its basic components. Normally a reverse engineer reads the disassembled software and then analyzes the underlying logic and structure.
The purposes of reverse engineering are multiple, such as:
- Debugging
- Enhancing Security
- Interoperability
- Replicating a competitor’s product
- etc
It is important to note that the legality of reverse engineering may vary depending on the jurisdiction and specific circumstances. So it is crucial to be aware of the relevant laws and regulations before undertaking such activities.
Reverse Engineering vs Malware Analysis
In one of my previous posts, I did a quick tour of the malware analysis, so you probably already know the main concepts of that.
In this section, we are going to explore the differences between these two disciplines so little known to most people.
While reverse engineering and malware analysis share some commonalities, it is essential to understand the distinctions between these two disciplines.
| Reverse Engineering | Malware Analysis | |
| What does it do? | breaking down software into its constituent components to study its design, architecture, and functionality. | focuses on examining malicious software, understanding its behaviour, and developing countermeasures to protect systems from potential threats. |
| Objectives | is often applied to enhance security, improve compatibility, or develop new features. | aims to secure systems from harmful software and mitigate the risks associated with cyberattacks |
| Obfuscation | In some cases to protect intellectual property the code is obfuscated, however that’s not a rule. | The dangerous malware which deserves an in-depth analysis always uses obfuscation and evasion techniques |
| Investigation Techniques | Static and Dynamic Analysis | Static and Dynamic Analysis |
Ultimately, these two fields are closely intertwined and often complement each other, providing valuable insights and knowledge for software developers, security experts, and researchers.
Concepts Of Reverse Engineering
In this section, we will delve into key concepts fundamental to reverse engineering, focusing specifically on the x86_64 architecture. These concepts form the foundation for a solid understanding of the reverse engineering process and will facilitate the exploration of practical applications. We will examine the x86_64 processor architecture, endianness, registers, calling conventions, and stack management in more detail.
The Instruction set
The x86_64 processor instruction set, also known as x64 or AMD64, is a 64-bit extension of the widely used x86 (32-bit) architecture. It combines the advantages of the x86 architecture’s extensive instruction set with the performance benefits and larger addressable memory space of 64-bit processing.
In other words, the x86_64 is a set of rules that tells a computer how to process information and perform tasks.
Think of it like a recipe book for your computer. Just as a recipe book has instructions for making different dishes, the x86_64 architecture provides instructions for the computer to complete various tasks, like playing games or opening websites.
Reverse engineering x86_64 software requires a strong understanding of its underlying architecture and instruction set, as well as familiarity with its 32-bit x86 counterpart.
Endianess
Endianness is a crucial aspect to consider when reverse engineering x86_64 software, as it determines the byte order in which data is stored in memory.
Just to better explain, let’s see a quick example.
Imagine you have a 4-byte integer in memory that looks like this:0x15 0xC1 0x90 0x4F
When an architecture uses big-endian order, the most significant byte is stored first in memory, and the least significant byte is stored last. So the 4-byte integer in our example would be stored in big-endian byte order as the below image shows:

If it uses a little-endian one, the least significant byte is stored first in memory, and the most significant byte is stored last. So the same 4-byte integer would be stored in little-endian byte order as:
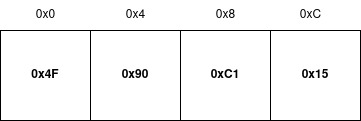
The incredibly common x86_64 architecture uses little-endian byte order.
I’m stressing this concept because understanding endianness, specifically the little-endian nature of x86_64, is critical when examining memory layouts and interpreting data during reverse engineering.
Registers
Registers are small, fast storage locations within the x86_64 processor that hold data and facilitate operations. The x86_64 architecture extends the x86’s register set, including 16 general-purpose registers (such as RAX, RBX, and RCX) and eight additional 128-bit SSE registers for floating-point operations. A solid grasp of these registers is necessary for comprehending the x86_64 assembly language and analyzing the flow of data within a program.
Here’s a list of some of the most important registers in the x86_64 architecture, along with a brief description:
- RAX: Accumulator Register – This is a general-purpose register primarily for arithmetic and data manipulation. It often stores the result of operations.
- RBX: Base Register – Another general-purpose register, RBX often holds the base address of a memory region in data manipulation operations.
- RCX: Count Register – The typical destination for loop counters and as an index in string operations. RCX is a general-purpose register as well.
- RDX: Data Register – RDX is a general-purpose register, it’s normally in charge of input/output and some arithmetic functions.
- RSI: Source Index – Mainly used for pointer operations, RSI holds the address of the source operand in memory-to-memory data transfers.
- RDI: Destination Index – Similar to RSI, RDI holds the address of the destination operand in memory-to-memory data transfers.
- RBP: Base Pointer – RBP is a pointer register that references a specific memory location relative to the current stack frame in the function call stack.
- RSP: Stack Pointer – This register points to the top of the stack, which is crucial for managing function calls, temporary storage, and local variables.
- RIP: Instruction Pointer – RIP stores the address of the next instruction to execute. It is essential for program flow control.
- R8 to R15: Additional General-Purpose Registers – These registers provide extra storage and flexibility for various operations in the x86_64 architecture.
- FLAGS (RFLAGS): Flags Register – iT contains status flags that indicate the result of previous operations or the current state of the CPU. Some common flags are Zero Flag (ZF), Carry Flag (CF), Sign Flag (SF), and Overflow Flag (OF).
Calling Conventions
A calling convention is a set of rules that dictate how functions receive and return data. These rules help manage the flow of information between functions and ensure that both the caller (the function that calls another function) and the callee (the function being called) know how to exchange data properly.
Here’s a brief introduction to CDECL, syscall, and System V AMD64 ABI calling conventions:
- CDECL: This is a popular calling convention used in C programs. CDECL wants function arguments on the stack in reverse order (from right to left), and the caller is responsible for cleaning up the stack after the function call. It’s standard within the beginner CTFs like picoCTF.
- syscall: this convention varies between operating systems but typically involves placing system call numbers and arguments in specific registers before triggering a software interrupt to call the system function.
- System V AMD64 ABI: is the standard calling convention for x86_64 systems in Unix-like operating systems, such as Linux and macOS. In this convention, the first six integer or pointer arguments must go in specific registers (RDI, RSI, RDX, RCX, R8, R9), and the remaining arguments on the stack.
If there are floating-point arguments, they are passed in XMM registers.
Caller-saved and Callee-Saved registers
Caller-saved and callee-saved registers are two categories of registers that help maintain data consistency and proper function operation during function calls:
- Caller-saved registers: These are registers that the callee may modify during its execution. The caller function is responsible for saving the contents of these registers before making a function call and restoring them after the call.
- Callee-saved registers: These are registers that the callee function must preserve during its execution. If the callee needs to use these registers, it should save their original values (typically on the stack) before using them and restore them before returning to the caller function.
The Stack and Heap
Stack and heap are two memory regions where to store and manage data. They serve different purposes and have different ways of allocating and deallocating memory.
Stack:
- The stack is a region of memory that stores function call-related data, such as local variables and function call return addresses.
- It follows a Last-In, First-Out (LIFO) structure, meaning the most recently added data is the first to be removed.
- The system automatically manages the stack, with memory allocation and deallocation happening on function call and return.
- It has a fixed size, determined at compile time or program startup, and if the stack size is exceeded (stack overflow), it can lead to crashes or undefined behaviour.
- Stack memory allocation is typically faster and more efficient because the system handles it.
Heap:
- The heap is a region of memory for dynamic memory allocation, allowing programs to request memory at runtime.
- In the memory on the heap, there are generally objects or data structures that have a longer lifetime than a single function call or require an indeterminate size at compile time.
- Heap allocation and deallocation must be explicitly managed by the programmer, using functions like
malloc,calloc, orfreein C, or using constructors and destructors in languages like C++. - The heap has a more flexible size, and it can grow or shrink during the program execution as needed. However, if the heap becomes too fragmented or runs out of available memory, allocation may fail.
- Heap memory allocation is generally slower and less efficient because it involves additional overhead for managing memory.
The stack and heap grow in opposite directions. In most systems, the stack starts at a high memory address and grows towards lower addresses, while the heap starts at a low memory address and grows towards higher addresses. This organization helps prevent them from overlapping, as long as there is enough memory available.
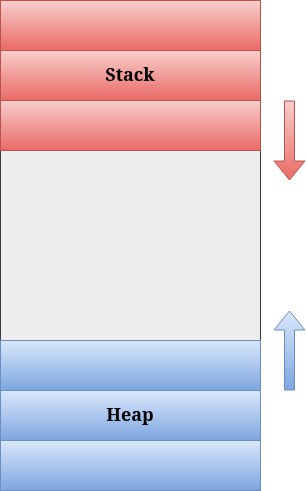
In summary, the stack is used for short-lived, fixed-size data and automatically managed function call-related information. While the heap stores global, dynamically-sized data that requires explicit memory management by the programmer.
Conclusion
In conclusion, we hope this article has offered valuable insights and a deeper understanding of software analysis. Keep an eye out for our upcoming posts on this topic, which will delve into various aspects of reverse engineering and provide further insights into this crucial domain.
At Stackzero, our goal is to share knowledge, foster growth, and facilitate learning for everyone, from beginners to experienced professionals. We encourage you to stay connected with our blog as we delve into various aspects of cybersecurity:
- Reverse engineering
- Malware analysis
- Ethical hacking
We will keep providing informative content, practical examples, and in-depth analysis! Our goal is to enrich your understanding and help you develop new skills in this ever-changing field.
In addition, we invite you to connect with us on our social media channels, where we share:
- Updates
- Interesting articles
- Relevant cybersecurity news
Engage with our community, participate in discussions, and stay informed about the latest trends and developments in cybersecurity!
We believe that, together, we can make a positive impact on the world of cybersecurity by learning and sharing.
Join us on this exciting journey, and let’s work towards a safer and more secure digital future.







