Welcome back to our series on the GNU Debugger (GDB) and its applications in tackling the PicoCTF challenges. If you’re joining us for the first time, we recommend revisiting our guide on the Registration Guide and GDB Baby Step 1 Challenge.
This introductory piece provides a comprehensive overview of GDB, its functionalities, and its significance in the realm of Linux debugging.
Continuing our journey, we are now poised to take on the GDB Baby Step 2 Challenge. While our objective remains the same – to determine the value within the ‘EAX’ register at the end of the ‘main’ function – the approach differs. This time, we engage with the program dynamically, executing and observing its behaviour in real-time. Ready to dive in? Let’s proceed.
Recap of GDB Baby Step 1
In the GDB Baby Step 1 Challenge, we traversed the basics of GDB operations. We aimed to decipher the decimal equivalent of the value stored in the ‘EAX’ register as the ‘main’ function culminated. While the task was achievable via straightforward disassembly, we opted for an extra layer of understanding, experimenting with basic debugging techniques.
Through this process, we paused program execution, set strategic breakpoints, and analyzed the real-time behaviour of the code. This practice offered valuable insight into the dynamism of debugging and set the groundwork for more complex operations in the realm of reverse engineering.
Armed with the foundational knowledge of GDB functionalities, we are now well-positioned to navigate the complexities of the upcoming challenge. Let’s gear up for a deeper exploration of GDB’s practical usage as we step into the Baby Step 2 Challenge.
Prerequisites for the Challenge
Before plunging into the intricacies of the GDB Baby Step 2 Challenge, it’s essential to have a solid understanding of a few core concepts in the field of reverse engineering. Being well-versed in these areas would significantly enhance your ability to solve the challenge efficiently and effectively.
The key prerequisite is an understanding of registers and calling conventions. In simple terms, registers are temporary storage spots in the CPU where the program stores important data, and calling conventions dictate how functions get their arguments from these registers. A thorough comprehension of these concepts is crucial in navigating the debugging journey seamlessly. For an in-depth exploration of these topics, we highly recommend our detailed guide on reverse engineering.
In addition, an introductory understanding of GDB and its operations forms an essential component of the knowledge base required for the challenge. This includes understanding how to install GDB, navigate its interface, disassemble programs, and execute them line by line. To solidify your foundation in these areas, we invite you to peruse our first guide focused on GDB within the context of a PicoCTF challenge.
With these prerequisites in place, you’ll find yourself well-equipped to conquer the GDB Baby Step 2 Challenge.
Remember, the journey of reverse engineering is all about continuous learning and exploration. So, keep exploring, keep experimenting, and let’s gear up for the exciting journey ahead.
Preparing for the Challenge
Prior to diving into the challenge, we must ensure the readiness of our debugging environment. The first task is to procure the challenge file from the PicoCTF platform.
To do that, let’s find the challenge named “GDB Baby Step 2” in the reverse engineering section you can see in the screenshot:

With our previous guide, you would have already set up GDB on your Linux machine. As we did there, our choice fell on a Kali Linux machine which is more than sufficient for the purpose.
If not, our introductory guide on GDB provides comprehensive instructions for the setup.
Download the file (debugger0_b) into your working directory in your chosen machine with GDB and then open a terminal pointing there.
With the environment prepared and the challenge file at hand. We are set to embark on the journey of GDB debugging.
As we progress, the aim is not only to successfully solve the challenge but also to enhance our understanding of GDB’s operations.
Stay focused, and let’s navigate our way to the solution to the Challenge.
Unlocking the Challenge: Extracting the Flag
Overview Of The Challenge
With our prerequisites firmly in place and a good grasp of the foundational concepts, let’s roll up our sleeves and delve into the heart of the GDB Baby Step 2 Challenge – reverse engineering the code.
First off, start our program under GDB, using this command in your terminal
gdb debugger0_bRemember to set your assembly syntax to Intel, with
set disassembly-flavor intelproviding a more comprehensible assembly language layout (that’s just my opinion if you prefer you can leave the AT&T syntax).
Next up, we need to identify our target function. Use the
info functionscommand to list all functions in the program.
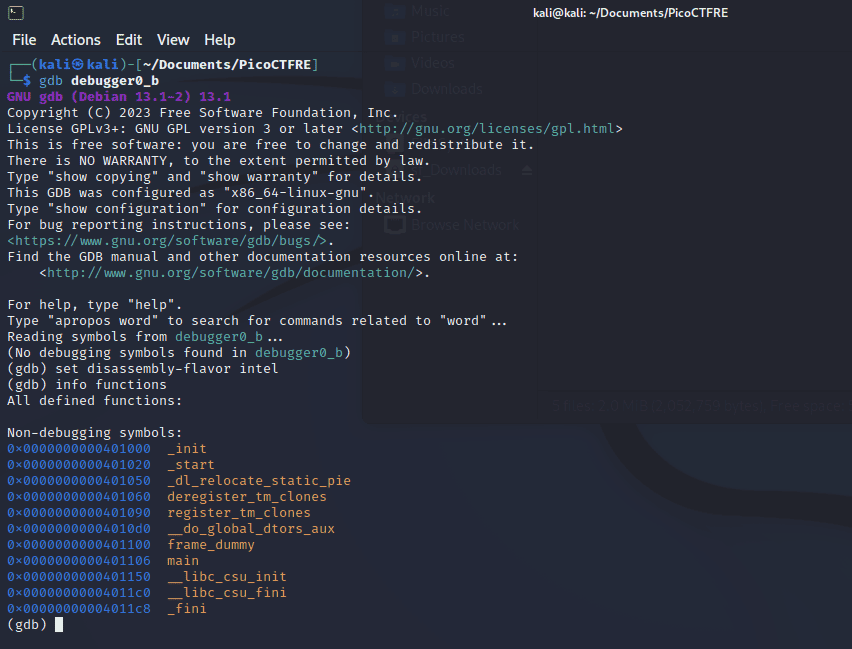
From the resulting output, it’s evident that our function of interest is main. To disassemble it, you can simply use
disassemble mainYou’ll notice the code here appears more complex than in the previous challenge.
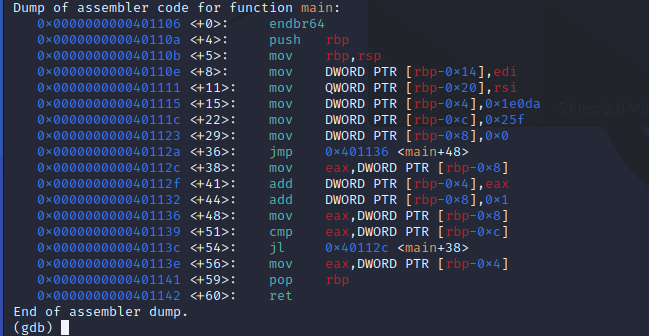
However, given the nature of Capture The Flag (CTF) competitions, time is of the essence. As suggested by the challenge description, we’re focusing on the dynamic analysis aspect.
Debugging in practice
Start by setting a breakpoint at the ‘main’ function using
break mainFollowing this, to get a clearer picture of the assembly code, set the layout to assembly using
layout asmand then run the program using the command:
runThe execution halts at the first instruction of ‘main’, but we need the content of the EAX register at the function’s end. The function ends with the ‘ret’ instruction at address 0x401142.

The game plan? Set a breakpoint at 0x401142 (the address of the return instruction), continue the execution, and then extract the decimal value of the EAX register.
Set the breakpoint at 0x401142 using the:
break *0x401142with the asterisk signifying a memory address.
Now, let’s let the program run its course with the command (abbreviation for “continue”):
cAs you’ll see, the pointer now points to the desired address. If you’re unsure, you can check the content of the instruction pointer register (RIP) using:
info registers rip
With the program halted at the correct location, it’s time to retrieve the value of the EAX register. Use:
print/d $eaxVoila, here’s the result!
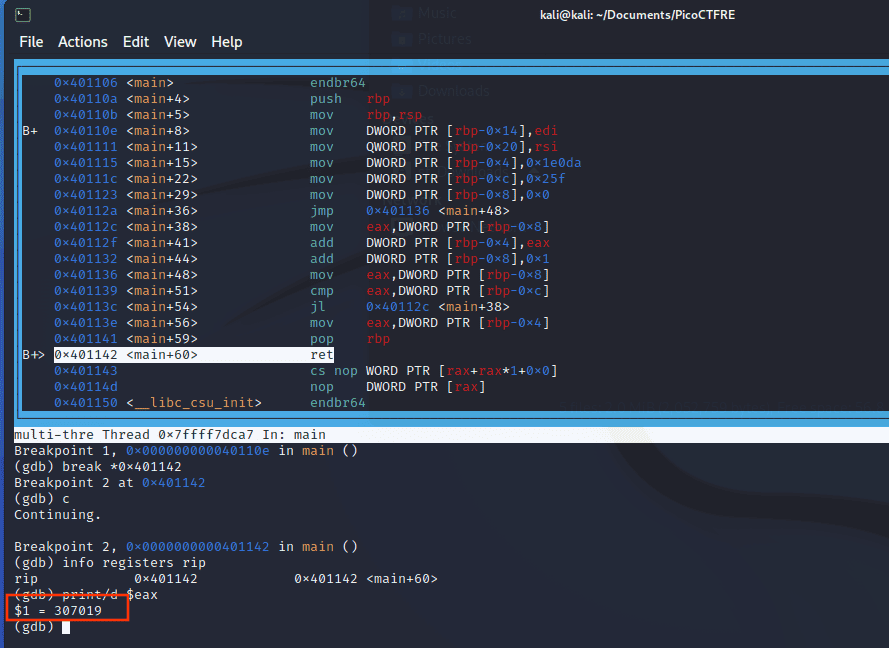
The flag we’ve been hunting for is picoCTF{307019}.
Now, simply input this into the challenging field, and bask in the glory of a job well done!

By methodically breaking down the steps and moving through the process, you’ve cracked the GDB Baby Step 2 Challenge.
Conclusion
We’ve reached the end of our dive into the GDB Baby Step 2 Challenge, yet this represents just one step in your larger journey towards mastering reverse engineering and the GDB debugger. By applying the skills and knowledge gained, you’ve successfully navigated the task, unlocking another layer of understanding in the process.
The true beauty of such challenges lies in the opportunity they provide to broaden your skillset and deepen your comprehension of intricate software concepts. GDB, with its immense capabilities, is a tool that continues to unravel its depth with each use. Today, you’ve scratched a little deeper beneath the surface, but there’s a world of potential still waiting to be explored.
As you continue your journey, always remember that progress comes with practice, and mastery with consistency. With each challenge you take on, you’re not only getting better at solving it but also enhancing your understanding of how software works at a granular level. In the vast landscape of software debugging and reverse engineering, every small step forward, like the one you’ve taken today, matters.
The world of reverse engineering is an ever-evolving arena, and at StackZero, we’re committed to helping you stay at the forefront. Continue to tune in to our blog and follow us on our social media channels for a constant stream of insightful content and engaging challenges that’ll keep your learning momentum alive.
Together, let’s take more strides towards mastering the art and science of reverse engineering. Let the curiosity within you guide your steps, and let the challenges we present stir your desire to learn, grow, and conquer.
Until next time, keep exploring, keep learning, and most importantly, keep stepping ahead.







