Are you a beginner in the intriguing world of reverse engineering? Or perhaps you’re keen to delve into the workings of Linux’s GDB debugger? Either way, we’ve got you covered. Welcome to Stackzero, your one-stop destination for all things related to these topics. Here, we’ve curated a wealth of resources to guide your learning journey.
If you’re just starting out, we recommend our foundation guides on Reverse Engineering, GDB and maybe the Mastering PicoCTF: Your Ultimate Registration Guide!
These easy-to-understand tutorials cover the basics of reverse engineering and using the GDB debugger. So why not take a few moments to read through them? It will give you the background knowledge you need to tackle the more complex challenges that lie ahead.
Today, we’re going to take on a particular challenge – the PicoCTF “GDB Baby Step 1”.
It’s an exciting task that tests your understanding of both reverse engineering and the GDB debugger.
Don’t worry if you’re new to these concepts, we’ll walk through it step by step.
Ready to embark on this exciting journey of discovery? Let’s jump in!
Decoding GDB: A Primer to the GNU Debugger
The world of programming and debugging can seem complex. Fortunately, the GNU Debugger, known as GDB, is here to help. GDB is a useful tool for programmers, especially those using Linux systems.
In essence, it lets you see what’s happening inside your program while it’s running. You can explore your code in depth, just like examining a machine’s parts closely.
With GDB, you can disassemble code. This means breaking a program down into smaller parts, a handy feature when working with low-level languages or inspecting compiled programs.
GDB also lets you inspect registers – high-speed storage areas in a computer’s CPU. Knowing what’s in these registers can give you insight into your program’s operation.
Moreover, GDB allows you to set breakpoints. This is like pausing a film to understand a crucial scene. Breakpoints let you pause program execution at specific places, helping you understand how your code works.
In summary, GDB is more than a debugging tool. It’s a platform that enhances your ability to interact with and understand your software. Whether you’re a developer, a cybersecurity enthusiast, or a coding learner, GDB is a tool you’ll want to learn.
So, if you’re ready to explore programs in a new way, let’s get started with GDB.
Preparations and File Analysis
Kickstart this adventurous journey by firing up your Kali Linux virtual machine.
Navigate to the PicoCTF website, locate the challenge named “GDB Baby Step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the description, and download the file.

After downloading, shift this file into your dedicated workspace where we can take our time to analyse it. Curious to know more about the file?
So run:
$ file debugger0_a
debugger0_a: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=15a10290db2cd2ec0c123cf80b88ed7d7f5cf9ff, for GNU/Linux 3.2.0, not stripped
Voila! You have your answer. It’s an Executable and Linkable Format (ELF) file, as you might have guessed. But thanks to that useful command you also know that it’s a 64-bit executable and that’s not stripped (so we can see its symbols).
The Magic of Disassembling with GDB
Enter the fascinating world of disassembly with GDB. Let’s begin by opening the downloaded file by passing it as an argument to GDB:
gdb debugger0_aWant to get an overview of all the functions? Just type:
info functionsAs shown in the following screenshot, we have confirm that this file isn’t stripped, and all function names are in plain sight.

Our prime target here is the ‘main‘ function (address 0x1129).
Before we proceed, it’s essential to know that GDB’s syntax is set to AT&T by default. Are you more comfortable with Intel syntax like most of us?
You can easily change the setting by typing:
set disassembly-flavor intelHaving done that, we’re now set to uncover the assembly code by entering
disassemble mainThe disassembly process unveils the following:

The crux of this challenge is to discover the EAX register value. From the disassembled code, we see that the number 0x86342 is moved into this register.
However, the number is in hexadecimal format, and we need to convert it to a decimal format.
Let’s embark on this conversion journey, that’s an easy task with the help of our beloved python.
Open a new terminal and type
pythonThen, to transform the hexadecimal value into a decimal, punch in:
print(int(0x86342))Behold the decimal equivalent, 549698!
We’ve now arrived at our flag: picoCTF{549698}.
Just copy and paste this into the input field on the PicoCTF website.
Mission accomplished!
Alternative Path: Debugging the Executable
For those who love exploring alternative routes, let’s solve this challenge through debugging.
Begin by setting a breakpoint at the main entry point.
Simply type:
break main Next
runAnd then:
layout asmfor more detailed visualization.
Refer to the screenshot below for clarity:

To execute instructions up to the 'ret' instruction (<main+21>), write:
nifor the next instruction, and then the “Enter” button until you reach the target instruction.
Now, reveal the EAX register’s decimal value by typing:
print/d $eaxHere’s the screenshot displaying the value:
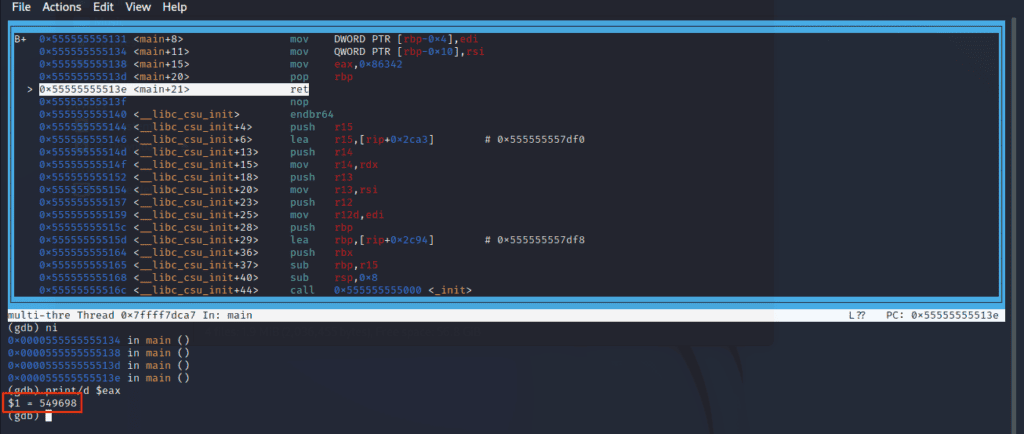
Voila! As expected, the decimal value is 549698, corroborating our earlier findings.
This reaffirms that our flag remains steadfast at picoCTF{549698}.
Conclusion
To put it simply, GDB is an essential tool in your toolkit for reverse engineering. It’s crucial for taking apart and investigating code, making it an invaluable resource for solving puzzles like PicoCTF’s “GDB Baby Step 1”. This journey we’ve taken, uncovering the value in the EAX register, making sense of the ELF file, and cracking the challenge is a perfect example of GDB’s power.
Are you feeling a rush of achievement? That’s the beauty of learning! But remember, this is just the beginning. The field of reverse engineering is vast and full of endless mysteries waiting to be unlocked.
Are you eager to keep exploring? We’re excited to share that journey with you. Stay in the loop with all the latest learning opportunities and challenges by following us at Stackzero and connecting with us on our social media profiles.
Remember, the world of learning is vast and open to all. Every expert was once a beginner too. So, keep exploring, keep learning, and continue to uncover the exciting puzzles that reverse engineering offers. I think that CTFs are the best way to learn and have fun at the same time.
The more you learn, the more fascinating it becomes. So, let’s keep that curiosity alive and dive deeper into the world of reverse engineering together!







