In the digital age, cybersecurity is essential in keeping our personal and professional data safe. To sharpen their skills, cybersecurity enthusiasts often participate in events known as Capture the Flag (CTF) competitions. In this article, we will delve into the world of CTFs, focusing on PicoCTF, a competition specifically designed to help beginners learn and practice cybersecurity skills.
What is a CTF?
Capture the Flag (CTF) is a type of computer security competition that challenges participants to test and expand their skills in various cybersecurity areas, such as cryptography, reverse engineering, and web exploitation. In a typical CTF, participants have to solve challenges and find hidden “flags” that signify a successful completion. CTFs come in various formats, each designed to offer unique experiences and cater to different skill levels and interests.
- Jeopardy-style: participants solve individual challenges categorized by topics and difficulty levels. Each challenge has its own point value, and the objective is to accumulate the highest score possible by solving the challenges. This format is particularly beginner-friendly, as it allows participants to focus on their areas of interest and expertise without facing direct competition from other teams.
- Attack-Defense: this format pits teams against each other in real-time. Each team is given a set of vulnerable services to defend while simultaneously trying to exploit vulnerabilities in other teams’ services. This format closely resembles real-world cybersecurity scenarios and demands strong teamwork, communication, and strategy to succeed.
- King of the Hill (KotH): participants compete to gain and maintain control over a specific target system, known as the “hill.” The team that maintains control of the target system for the longest time will be the winner. This format emphasizes persistence, adaptability, and resourcefulness in addition to technical skills.
- Mixed Format: Some CTF competitions combine elements of various formats to create a unique and dynamic experience. These mixed-format events often include multiple stages, with each stage featuring different types of challenges and formats.
Does CTF help to learn?
CTF competitions are excellent learning opportunities for both beginners and experienced cybersecurity enthusiasts. They offer a practical and interactive environment for participants to apply their knowledge and learn new skills. Participants can strengthen their problem-solving abilities, teamwork, and communication while exploring various aspects of computer security. Gamification significantly enhances engagement and information retention in these challenges.
Is CTF good for cybersecurity?
CTFs not only help participants learn, but they also contribute to the broader cybersecurity community. By simulating real-world threats and scenarios, CTFs help identify and fix vulnerabilities in systems and software. Moreover, CTFs can inspire future cybersecurity professionals and promote collaboration among experts to develop innovative solutions to emerging threats.
Does the CTF need programming and which programming languages are the best?
While programming skills can be advantageous in CTF competitions, it is not always required. CTF challenges vary in difficulty and topic, allowing participants to focus on their areas of interest or expertise. However, a basic understanding of programming languages like Python, C, or JavaScript can prove useful in solving certain challenges. Python, in particular, is popular due to its readability, versatility, and wide range of libraries suited for cybersecurity tasks. On the other hand, C knowledge can be very valuable in reverse engineering and binary exploitation challenges.
What is PicoCTF?
PicoCTF is a cybersecurity competition designed specifically for beginners and students. PicoCTF provides an engaging and gamified platform for participants to learn cybersecurity concepts and skills. Challenges in PicoCTF cover a wide range of topics, such as binary exploitation, cryptography, and forensics, and are designed to gradually increase in difficulty to accommodate participants with varying skill levels.
Is PicoCTF free?
Yes, PicoCTF is entirely free to participate in. The platform aims to make cybersecurity education accessible to a broad audience, including students and those interested in entering the field. PicoCTF’s extensive library of challenges and resources is available for participants to explore and learn from at any time, not just during the annual competition.
How do I join PicoCTF?
Are you wondering if you’re eligible for PicoCTF?
The answer is most likely yes. PicoCTF caters to everyone interested in cybersecurity, from 13-year-olds to college students.
So, let’s get started!
First, visit the PicoCTF login page at https://play.picoctf.org/login. Click “Sign up” and fill out the registration form with your information.

Once you’ve confirmed your email, you’re ready to begin.
For a more detailed tutorial on how to register, you can take a look at our article Mastering PicoCTF: Your Ultimate Registration Guide!
General Challenges
To get a feel for the platform, try out some general challenges. Log in, click on the “Practice” button in the top menu, and then select “General Skills” from the left sidebar menu.

Obedient Cat
Let’s start with the “Obedient Cat” challenge, worth 5 points (points often reflect difficulty). Click on the challenge to view its description, download link (green rectangle), and hints (red rectangle):
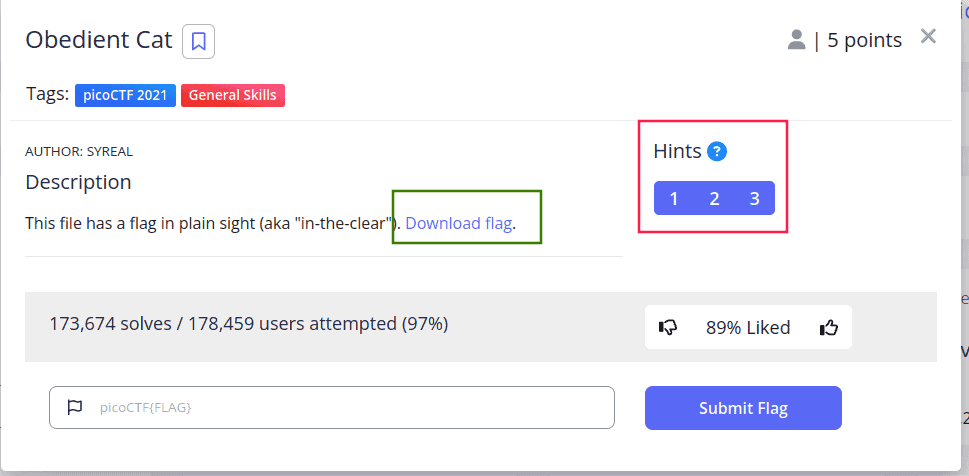
Download the text file, which contains the following string:
picoCTF{s4n1ty_v3r1f13d_28e8376d}This string, in the platform’s standard flag format, is our solution.
Enter it into the input text field and submit the flag!
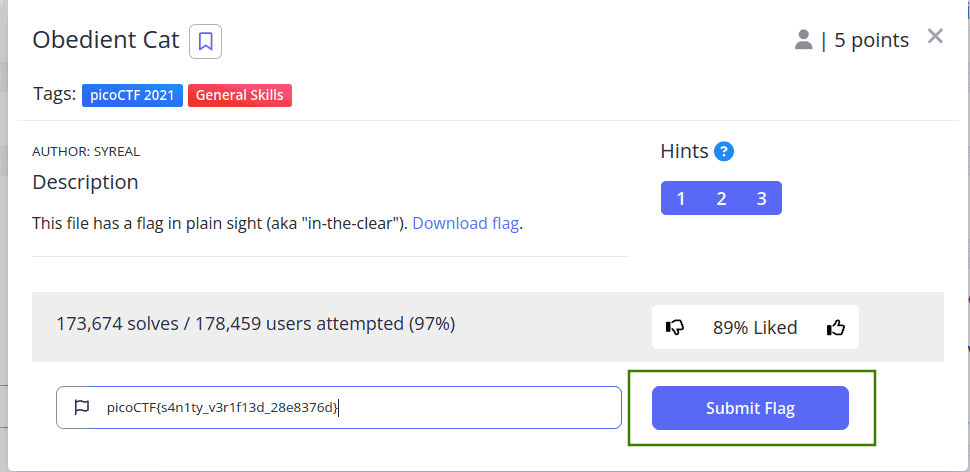
And the first challenge is done, now we have learned how is a flag and where to put it once we find it.
Congratulations! You’ve completed the first challenge, learned what a flag looks like, and discovered where to submit it once found.
Python Wrangling
The next challenge, “Python Wrangling,” involves running a Python script.
Ensure you have Kali Linux installed on your system or Python from the official website based on your operating system.
Challenge description:
Python scripts are invoked kind of like programs in the Terminal… Can you run this Python script using this password to get the flag?
Three files are included:
- ende.py: a Python script
- pw.txt: a password
- flag.txt.en: the encrypted flag
Download the files and open a terminal in their directory. Type:
python ende.pyThe response will be:
Usage: ende.py (-e/-d) [file]Options:
- -e: encrypt
- -d: decrypt
To decrypt flag.txt.en, type:
python ende.py -d flag.txt.enEnter the password from pw.txt:
dbd1bea4dbd1bea4dbd1bea4dbd1bea4The script will return the flag.

Let’s insert it into the input field and press submit. Now the challenge is done!
Wave a flag
The next challenge, “Wave a Flag,” features this description:
Can you invoke help flags for a tool or binary? This program has extraordinarily helpful information…
Download the file “warm” to your Kali Linux machine. Open a terminal in the file’s directory and type:
file warmYou’ll see it’s a 64-bit ELF (Executable Linux Format). Ensure the file has to execute permission by running:
sudo chmod +x warmThen, execute the file with:
./warmThe output is:
Hello user! Pass me a -h to learn what I can do!Following the tip, run:
./warm -hThe response reveals the flag:
picoCTF{b1scu1ts_4nd_gr4vy_18788aaa}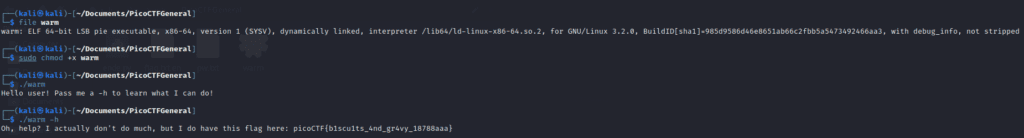
Submit the flag to complete this simple CTF challenge!
Conclusion
As we have explored the fascinating world of Capture the Flag competitions and the opportunities they offer for skill development and collaboration, it’s clear that CTFs, especially beginner-friendly events like PicoCTF, are an integral part of the cybersecurity community.
By participating in these competitions, individuals can not only enhance their understanding of cybersecurity but also contribute to the community and prepare themselves for rewarding careers in this ever-growing field. The significance of cybersecurity will only continue to grow, and we invite you to join us on this journey to stay informed, educated, and engaged.
To stay up to date on the latest trends and developments in the world of cybersecurity and CTFs, don’t forget to follow our blog. We look forward to exploring this exciting domain together and building a more secure digital future for all.







